Customers who are serious about security are looking for a Splunk + Ziften solution.


Overview
Ziften’s lightweight, non-driver-based data collector continuously monitors endpoints and integrates natively with Splunk to push all endpoint data directly into the Splunk index. Customers currently using the combination are finding enhanced security capabilities to prevent, detect, and respond to security threats at the endpoint, in a faster and more cost effective manner. In most cases customers utilizing continuous endpoint visibility see a reduction of incident response time near 70%.
Ziften is always on to protect to the end; learn how the combination with Splunk is defining the future of security.
To get started with a no-hassle/no-commit proof of concept contact one of our Sales Engineers now.
- Continuous endpoint visibility enables real-time detection and response, along with incident prevention
- Sophisticated security analytics assess and evaluate dynamic risk indicators and anomalies to prioritize findings for security teams
- Innovative and valuable intelligence to span across both security and operational teams to enhance long-term value
- Amplification of Splunk Enterprise Security and compliance with Splunk’s Common Information Model (CIM), to easily integrate with both Splunk apps and custom built apps
Ziften App for Splunk
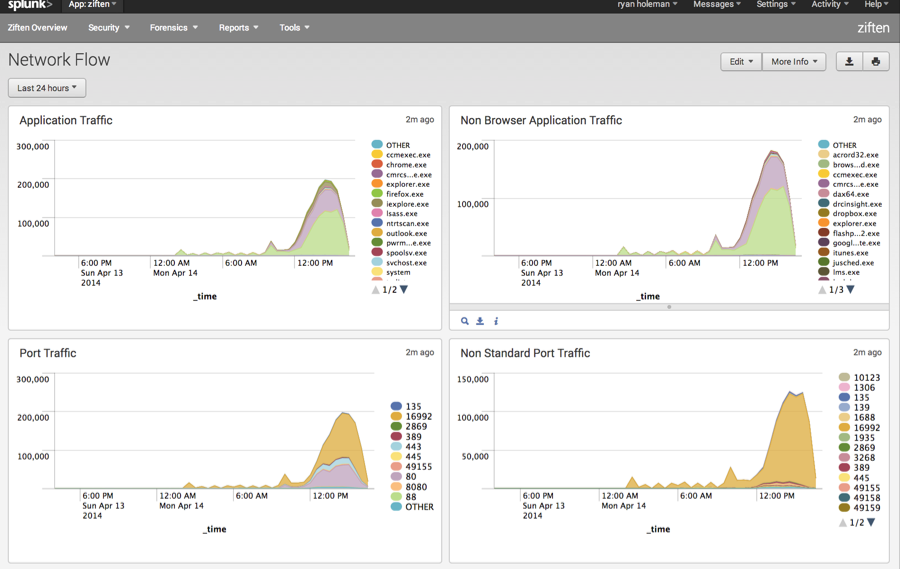
The Ziften for Splunk App provides native integration of comprehensive endpoint visibility into Splunk, with the ability to combine that information with threat feeds and network intelligence for an end-to-end view of indicators of compromise.
Continuous Monitoring
Continuous Visibility and IntelligenceZiften’s endpoint detection and response delivers continuous visibility and intelligence of endpoints, enabling end-to-end prevention, detection, and response for today’s advanced threats. By combining endpoint visibility with other solutions in the security ecosystem (such as SIEM, NetFlow, Firewalls, etc.), Ziften’s Open Visibility™ provides security teams a truly holistic view of their environment to help address advanced threats.
Ziften’s lightweight, minimal impact collector monitors endpoint devices and provides continuous visibility into policy and compliance violations, deployment and usage of vulnerable applications, and Indicators Of Compromise (IOC) for addressing advanced threats and risks associated with the behaviors from endpoint assets. Ziften issues alerts in real-time when IOCs or elevated risk occur.
Ziften ZFlow™ is an exclusive Ziften feature, enabling organizations to attain the last-mile network visibility that has been lacking to date. This includes the context and attribution of who, what, and how endpoint network connections were made. This new visibility greatly enables organizations to improve their security posture and help to protect their reputation.
Prevent
Arm Yourself Against Cyber Security AttacksZiften raises the bar for attackers by identifying opportunities for organizations to reduce their surface area for attack, proactively alerts when security policies are violated, and monitors for usage of vulnerable applications. This real-time, Continuous Monitoring of endpoints helps to proactively identify a variety of Indicators of Compromise (IOCs) and elevated risks. Ziften’s endpoint intelligence enables reporting, alerting, and deep forensic investigation capabilities, delivering proactive security analysis to identify threats and nascent compromises before they spread across the enterprise.
Detect
Identify Potential Threats Before They SpreadTraditional Antivirus, Firewall, and Intrusion Detection Systems (IDS) are no longer sufficient against today’s advanced threats. Defending against the continuous onslaught of attacks on organizations requires continuous monitoring of endpoints and advanced analytics to identify and respond to security incidents as they unfold. Today, most targeted attacks are reported by third parties, many of which are discovered weeks, months, or even years after complete victimization of the organization.
Ziften goes beyond traditional Endpoint Protection Platform (EPP) defense to determine which systems or users are involved in the attack chain using longterm historical analysis of an organization’s endpoints. Ziften monitors, reports, and archives endpoint activity synopses that can be combined and correlated across endpoints, networks, and timeframes to reconstruct attack event sequences on any timescale. New intelligence may cast prior events in an entirely different light, requiring retrospective reanalysis and launching new lines of investigation and response. Legacy security solutions that only expose what appears significant or suspicious at that moment lack this essential reexamination capability.
Respond
Real Time and Efficient Incident ResponseDespite the best preventive measures, breaches are bound to occur. No amount of blocking and prevention can be 100% effective at stopping finding and stopping all threats. Industry analysts have suggested that security investments should rebalance from over-reliance on blocking towards enabling teams to respond in realtime as incidents are unfolding (incident response) and towards forensics that enable teams to go back in time to when the breach occurred and deconstruct how the breach unfolded. In either case, reducing time to response, and providing full kill-chain visibility is the key.
Ziften’s Endpoint Detection and Response solution helps analysis teams to reduce time to response by providing the necessary user, machine, and process data that delivers informed visibility and actionable intelligence. Security analysis teams handling both incident response as well as post-breach forensic analysis of sophisticated attacks benefit from Ziften’s ability to perform end-to-end response and get to the root cause of the incident, concurrently with the attack or retrospectively in the past.
Integrate
Ziften Open Visibility™ Extends Your Existing Security InvestmentsZiften’s Open Visibility extends and multiplies the value of existing systems when integrated as a shared component of the security infrastructure. Ziften provides APIs, connectors, and alerts to integrate Ziften’s endpoint context and attribution data with a variety of security solutions already in place in enterprise environments. Ziften leverages best of breed intelligence partners, providing integrations with firewall, Netflow, SIEM, ticketing systems, response tools, and other security solutions to support enterprise teams with deep analysis and results for actionable response to advanced threats.
